There is a setting in Windows Group Policy which will force lockscreen / locked screensaver after a machine considers itself inactive for a specified amount of time:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-inactivity-limit
This overrides all other related (e.g. screen saver) settings and PC-local settings. It’s located here in group policy:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
and while creating/linking group policy on a server:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options
Categories:
Group Policy
Windows OS-Level Issues
The simplest appears to be thus:
wmic computersystem where caption='oldcomputername' rename newcomputername
If it is run from an administrative CMD and the machine is in good talking relationship with its domain controller, the PC and also AD rename will complete. If either prerequisite is not met, the rename will fail. A non-admin attempt fails with code 5, DC availability fails with 1355.
There is also tool, part of the 2003 server reskit and included later on, which can do the rename of a desktop from a domain controller:
NETDOM RENAMECOMPUTER OLDNAME /newname:NEWNAME /userd:domain\domainadmin /passwordd:password /force /reboot:0
It causes a reboot of the target machine. /reboot:0 means no delay; the number is in seconds.
Categories:
Windows OS-Level Issues
Servers
Really good article here:
http://www.itquibbles.com/sql-sbsmonitoring-high-disk-usage/
Solves the problem of the database reaching max capacity, and also speeds things up in general.
Short version:
In SBS 2008, run the contents of this zip file in an administrative PowerShell window.
In SBS 2011, start this shell as administrator:
C:\Program Files\Windows Small Business Server\Bin\MoveDataPowerShellHost.exe
and then while in the shell, run the contents of this zip file.
If it says “1 row affected”, it’s done, and the messages will point out old MDF and LDF files to remove.
You may notice that the script linked here is just a tad different than the one on the itquibbles page; this one just adds the -force items mentioned as an option on that page.
Categories:
Windows OS-Level Issues
Performance
Categories:
Windows OS-Level Issues
Categories:
Windows Installer, Updates, Patching
Windows OS-Level Issues
Administrative processes, including CMD, don’t see mapped drive letters anymore, unless you do this:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee844140(v=ws.10)
In this registry area:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
create DWORD EnableLinkedConnections, value of 1.
Categories:
Windows OS-Level Issues
Integration services are no longer automatically installed or automatically available, to guests running operating systems older than 10, on hosts running 2016. They have to be installed by powershell or DISM, directly into the guest, not the host. I found DISM to work when powershell didn’t. The appropriate image addition is downloaded here:
https://support.microsoft.com/en-us/help/3071740/hyper-v-integration-components-update-for-windows-virtual-machines-tha
and then installed thus, e.g. for Windows 7/2008R2:
DISM /Online /Add-Package /PackagePath:C:\storage\windows6.x-hypervintegrationservices-x64.cab
Categories:
Virtual Machines & Environments
Windows OS-Level Issues
This is something new to Windows 10/2016, a C runtime library different than the redistributables. It is a required additional install for some things to run on OS before 10/2016.
www.microsoft.com/en-us/download/details.aspx?id=50410
Categories:
Windows OS-Level Issues
Windows Installer, Updates, Patching
First in a series on improving Windows Group Policy. This apply to the whole Group Policy milieu on a network, all domain controllers.
- Even if there is only one domain controller, change the replication from 180 minutes to 15 minutes. These are in the properties of the site links, in Active Directory Sites and Services, under Inter-Site Transport, under IP. If you have more than one site link enabled, do it for all. Obviously you should moderate carefully, if you are using SMTP or have bandwidth issues.
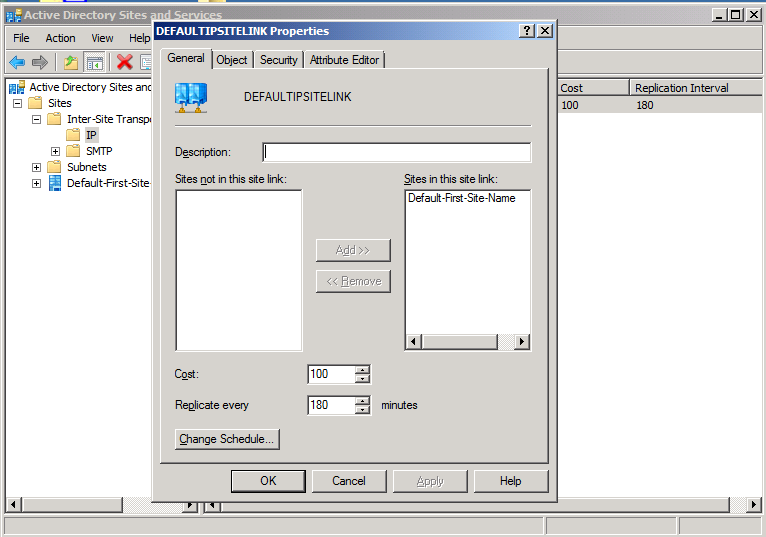
- Set services fdPHost and FDResPub as startup Automatic, from Manual.
- Add Subnet(s) to each Site in Active Directory Sites and Services. Then show subnets in the Group Policy Management Console, and map group policies there. Even if there is only one Site, this can help a lot.
Part II, Destrangulation, is here.
Categories:
Group Policy
Windows OS-Level Issues

Second in a series on improving Windows Group Policy.
One very common Group Policy strangulator shows up in Windows event logs as SceCli, event ID 1202. When Group Policy processing encounters this, it can prevent many things from occurring.
The error, specifically, is a nonexistent user or group present in a GP configuration item. For instance, most recently there was a Group Policy including a security item which included “Domain Uers”, a typo of “Domain Users”, deep in computer-level security items, and this prevented the policy from doing anything, even though there were other, equivalent, items in the same area. I’ll repeat, the typo item had to be removed, before the entire policy would do anything; group policy processing is apparently not able to treat a nonexistent referent as irrelevant.
Finding the item is interesting too. It requires a file of this name and location:
%SYSTEMROOT%\Security\Logs\winlogon.log
It may not exist. If not, or if it’s not up to date, browse to this registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions\{827D319E-6EAC-11D2-A4EA-00C04F79F83A}
and set DWORD ExtensionDebugLevel to 2. Then run gpupdate, and the file will be created. Then in administrative CMD, run:
FIND /I "Cannot find" %SYSTEMROOT%\Security\Logs\winlogon.log
The above will produce one or more invalid security group names or login names, included somewhere as a configuration item within a group policy. Once you have the name(s), run:
rsop.msc
and examine all of its tree carefully, to find the error. That will lead you to the spot in GPMC where you will find the bad entry, to fix. Once you have fixed, try your gpupdate again, and your policy will apply, unless something else is wrong!
Part III, Copying Files, is here.
Categories:
Group Policy
Windows OS-Level Issues
