If you find that login occurs, but no desktop just blackscreen, add the local users “Interactive” and “Authenticated Users” to the local group “Users”, i.e.:
net localgroup Users Interactive /add net localgroup Users "Authenticated Users" /add
If you find that login occurs, but no desktop just blackscreen, add the local users “Interactive” and “Authenticated Users” to the local group “Users”, i.e.:
net localgroup Users Interactive /add net localgroup Users "Authenticated Users" /add
Some articles:
https://msdn.microsoft.com/en-us/library/windows/desktop/ff384840(v=vs.85).aspx).aspx
https://blogs.technet.microsoft.com/filecab/2014/06/25/the-end-is-nigh-for-frs/
Recent versions of Outlook have something called Protected View, which can make handling of attachments more complicated. It can be turned off:
Something new:
When configuring a NIC for performance, it is very important first to bring the driver up to date; there are special needs in this area for Intel NICs. It will usually do quite a lot of good to bring a NIC driver up to date, if it’s not. In order to do a whole lot more good, after drivers are as good and as up to date as possible, please continue below!
These settings apply to hardware NICs only. There have been warnings posted by Microsoft against changing settings against virtual NICs. Concerning virtual machines, it is the host’s NICs which should be optimized as much as possible.
It may also be worthwhile to note, that several more steps were best and strongly recommended by Microsoft, differently and changing over time, in different versions of Windows before Vista/2008. The below are very good for Vista/2008 and thenceforth.
To continue. Some of the items below are in an “Advanced” tab and then “Performance” category in some manufacturers’ NIC properties, the location varies. Some of them may not be present in any given NIC. But except for a very few, most of the items below will be represented, and if you have one of those few you might think about an upgrade to a nice juicy Intel server-class PCIe NIC:
The Intel network interface card is a great piece of hardware. However, if its driver is not complete and/or not up to date, the whole PC or server in which it exists often will exhibit poor performance, hesitations, and web-site and LAN connection problems of many sorts. After this driver work is done, it’s a great idea to set it up for performance, but it is best to do the driver first.
First of all, here’s how to check if the driver is likely good — not necessarily up to date, but still likely to be good, and possibly not to be updated given the time and effort and onsite hands needed. Go to Device Manager, go to the properties of the NIC object, and pull up the Advanced tab. You should see something very like this:
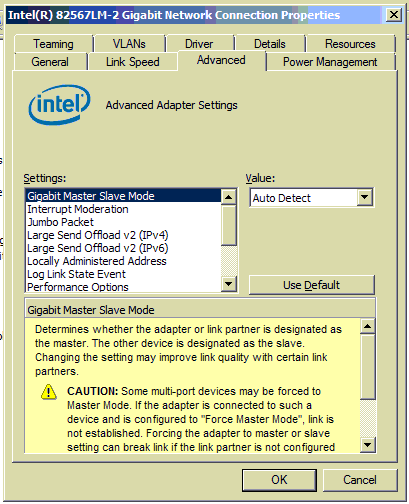
Note how the Settings list is fully populated, no blank space visible. If you see any blank space in that box, you are looking at a common problem situation. A great many PCs and some servers shipped by at least two major vendors, for many years, have been shipped with incomplete Intel NIC drivers. These drivers you really do want to replace ASAP with the most recent ones. In at least a few cases I have seen, the hardware vendor didn’t include any update on its web site; thus far, in every case, the download from Intel made things work far better.
At least one major vendor uses Intel NICs but places its own name in Device Manager, and thus far when tested the Intel downloads have worked just fine, and in one server, improved things tremendously.
There is also a circumstance where an Intel NIC has a reasonably recent driver, but the monitoring application’s add-ins are not installed or not working or not visible. Sometimes this occurs due to an unusual terminal server setup. It looks like this:
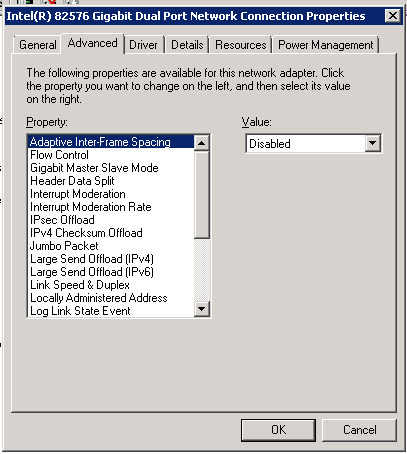
There are some Intel NICs, older ones, for which updates don’t exist for Microsoft’s newest operating systems. In this case, the screenshot immediately above will pertain, and this means the driver is as good as it will get.
But in most cases we have good work to do. Below are my steps for driver issues and updates.
If this is a server, this should be done in person or with BIOS-level GUI remote control, this is fairly radical change; you need to turn off server offerings while you’re doing this, and networking is temporarily halted twice during the actual successful install. For workstations, in-person may not be required, but hands onsite of some helpful kind are essential.
Here’s how to replace a self-signed Exchange certificate in the Exchange Shell.
First get the list with details:
Get-ExchangeCertificate | fl
You’ll see all of the certs, with expiration dates (“NotAfter”) and thumbprints. For each one that you need to replace, do this:
Get-ExchangeCertificate -thumbprint <thumbprintcontents> | New-ExchangeCertificate
Then say Yes.
LSIget contains an excellent RAID diagnostic system for LSI RAID, which includes 3ware. It produces a .7z archive with many different files inside. Mostly this is intended for LSI support tech usage, but it can help a lot when drive serial numbers don’t show up in the RAID console. To get this information from the archive, locate this file within and open it:
AdpAlllog_AO.txt
From the indefatigable Mike Martinez.
If you see a slew of 10016 errors in event logs, first try this:
http://support.microsoft.com/kb/920783
and then try this:
http://halfloaded.com/blog/sbs-2011-distributedcom-eventid-10016-fixed/
If you have to authenticate three times — once for for the portal, twice for RDP — try this:
http://tsbraindump.blogspot.com/2012/02/sbs-2011-remote-web-workplace-login.html
Lots of different methods and recommendations out there on the WWW for this. Here are two which appear to work, especially when used at the same time.
First, a VBS which has to be run from a group policy set to loopback mode:
''''''''''''''''''''
' Disable StickyKeys, Filter Keys, and ToggleKeys
''''''''''''''''''''
On Error Resume Next
Set ObjShell = Wscript.CreateObject("Wscript.Shell")
RegKey = "HKCU\Control Panel\Accessibility\"
ObjShell.RegWrite RegKey & "StickyKeys\Flags", "0", "REG_SZ"
ObjShell.RegWrite RegKey & "Keyboard Response\Flags", "0", "REG_SZ"
ObjShell.RegWrite RegKey & "ToggleKeys\Flags", "0", "REG_SZ"
ObjShell.RegDelete RegKey & "Keyboard Response\Last BounceKey Setting"
ObjShell.RegDelete RegKey & "Keyboard Response\Last Valid Delay"
ObjShell.RegDelete RegKey & "Keyboard Response\Last Valid Repeat"
ObjShell.RegDelete RegKey & "Keyboard Response\Last Valid Wait"
Set ObjShell = Nothing
And second, an ADM file which can import as a new administrative template into a group policy. It goes in automatically as a user-mode policy:
CLASS MACHINE CLASS USER CATEGORY "Control Panel" CATEGORY "Accessibility Lockdown" KEYNAME "Software\Policies\Accessibility" POLICY "Automatic Reset" KEYNAME "Software\Policies\Accessibility" VALUENAME "TimeoutConfig" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\Timeout" VALUENAME "Flags" VALUE "3" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\Timeout" VALUENAME "Flags" VALUE "2" END ACTIONLISTOFF PART "Timeout after idle for" DROPDOWNLIST REQUIRED KEYNAME "Control Panel\Accessibility\Timeout" VALUENAME "TimeToWait" ITEMLIST NAME "5 minutes" VALUE "300000" NAME "10 minutes" VALUE "600000" NAME "15 minutes" VALUE "900000" NAME "20 minutes" VALUE "1200000" NAME "25 minutes" VALUE "1500000" NAME "30 minutes" VALUE "1800000" END ITEMLIST END PART END POLICY POLICY "Disable StickyKeys (including shortcut)" KEYNAME "Software\Policies\Accessibility" VALUENAME "StickyKeysLockdown" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\StickyKeys" VALUENAME "Flags" VALUE "506" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\StickyKeys" VALUENAME "Flags" VALUE "510" END ACTIONLISTOFF END POLICY POLICY "Disable FilterKeys (including shortcut)" KEYNAME "Software\Policies\Accessibility" VALUENAME "FilterKeysLockdown" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\Keyboard Response" VALUENAME "Flags" VALUE "122" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\Keyboard Response" VALUENAME "Flags" VALUE "126" END ACTIONLISTOFF END POLICY POLICY "Disable ToggleKeys (including shortcut)" KEYNAME "Software\Policies\Accessibility" VALUENAME "ToggleKeysLockdown" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\ToggleKeys" VALUENAME "Flags" VALUE "58" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\ToggleKeys" VALUENAME "Flags" VALUE "62" END ACTIONLISTOFF END POLICY POLICY "Disable High Contrast (including shortcut)" KEYNAME "Software\Policies\Accessibility" VALUENAME "HighContrastLockdown" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\HighContrast" VALUENAME "Flags" VALUE "122" VALUENAME "Pre-High Contrast Scheme" VALUE "" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\HighContrast" VALUENAME "Flags" VALUE "126" END ACTIONLISTOFF END POLICY POLICY "Disable MouseKeys (including shortcut)" KEYNAME "Software\Policies\Accessibility" VALUENAME "MouseKeysLockdown" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 ACTIONLISTON KEYNAME "Control Panel\Accessibility\MouseKeys" VALUENAME "Flags" VALUE "58" END ACTIONLISTON ACTIONLISTOFF KEYNAME "Control Panel\Accessibility\MouseKeys" VALUENAME "Flags" VALUE "62" END ACTIONLISTOFF END POLICY END CATEGORY END CATEGORY