Windows 10 has some sort of automatic thing built in which is pretended to read our minds and decide for us which of our printers should be the default at any time. Needless to say this makes no sense at all, and causes lots of user frustration. To turn this off with Group Policy, browse to:
User Configuration -> Administrative Templates -> Control Panel -> Printers
and set “Turn off Windows default printer management” to Enabled.
Categories:
Group Policy
Printers & Printing
Normally, if a GPO is linked to an OU containing only computers, the user portion does not run. Loopback Mode makes it run. In GPMC, look here:
Computer Configuration, Policies, Administrative Templates, System, Group Policy, “Configure user Group Policy loopback processing mode”
Categories:
Group Policy
There is a strong tendency to want to use %username% as a macro in GPOs, to get the user’s name in. However, this doesn’t work in GPO. One has to use %LogonUser%. To get the whole list of macros, press F3 while the cursor is in the GPO setup field.
Categories:
Group Policy
First in a series on improving Windows Group Policy. This apply to the whole Group Policy milieu on a network, all domain controllers.
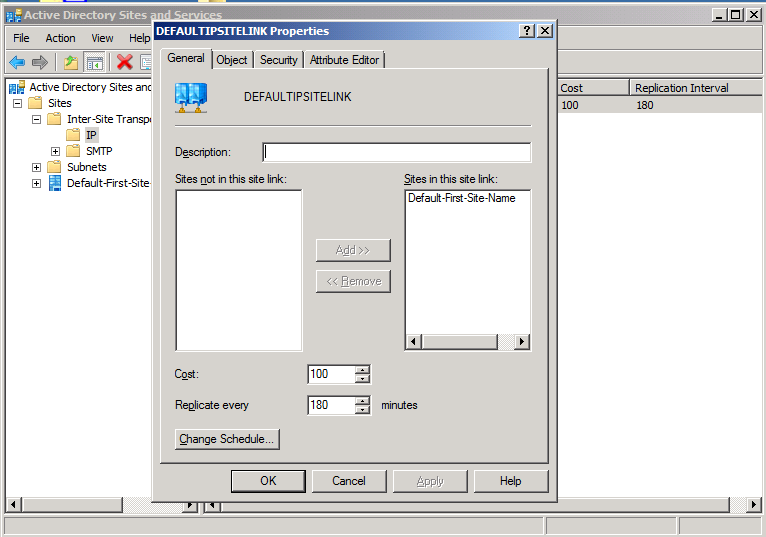
- Even if there is only one domain controller, change the replication from 180 minutes to 15 minutes. These are in the properties of the site links, in Active Directory Sites and Services, under Inter-Site Transport, under IP. If you have more than one site link enabled, do it for all. Obviously you should moderate carefully, if you are using SMTP or have bandwidth issues.
- Set services fdPHost and FDResPub as startup Automatic, from Manual.
- Add Subnet(s) to each Site in Active Directory Sites and Services. Then show subnets in the Group Policy Management Console, and map group policies there. Even if there is only one Site, this can help a lot.
Part II, Destrangulation, is here.
Categories:
Group Policy
Windows OS-Level Issues

Third in a series on improving Windows Group Policy.
Group Policy can and sometimes needs to copy files. If it fails, when you run this command:
GPRESULT /H gpresult.html /F
and look at gpresult.html in a web browser, you may see a permissions error, 0×80070005. This is commonly because your source file is not readable. To make this right, working advice appears to be to give read-only access to the source location, to “Authenticated Users”. Obviously this is not secure enough for some applications of this, but at the moment it is not clear what will work. “NETWORK” does not work, “SYSTEM” does not work.
But this page is a work in progress, the above permissions are clearly not satisfactory for many circumstances.
Reportedly, for user-level group policy items, the group policy engine runs with the permissions of the particular user logging in. But this does not make sense with the above, because any user logging in will be a member of “Authenticated Users”. So the engine must run as some other authenticated user, given that the user is apparently not counted as “logged in” while the engine is doing the above.
For computer-level items, the group policy engine runs with the permissions of the computer itself. This means that file copying may be quite a lot more reliable if it can be done without user information, e.g., to the public desktop et cetera. This should work by adding the security group “Domain Computers” as read-only to the source share.
Categories:
Group Policy

Second in a series on improving Windows Group Policy.
One very common Group Policy strangulator shows up in Windows event logs as SceCli, event ID 1202. When Group Policy processing encounters this, it can prevent many things from occurring.
The error, specifically, is a nonexistent user or group present in a GP configuration item. For instance, most recently there was a Group Policy including a security item which included “Domain Uers”, a typo of “Domain Users”, deep in computer-level security items, and this prevented the policy from doing anything, even though there were other, equivalent, items in the same area. I’ll repeat, the typo item had to be removed, before the entire policy would do anything; group policy processing is apparently not able to treat a nonexistent referent as irrelevant.
Finding the item is interesting too. It requires a file of this name and location:
%SYSTEMROOT%\Security\Logs\winlogon.log
It may not exist. If not, or if it’s not up to date, browse to this registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions\{827D319E-6EAC-11D2-A4EA-00C04F79F83A}
and set DWORD ExtensionDebugLevel to 2. Then run gpupdate, and the file will be created. Then in administrative CMD, run:
FIND /I "Cannot find" %SYSTEMROOT%\Security\Logs\winlogon.log
The above will produce one or more invalid security group names or login names, included somewhere as a configuration item within a group policy. Once you have the name(s), run:
rsop.msc
and examine all of its tree carefully, to find the error. That will lead you to the spot in GPMC where you will find the bad entry, to fix. Once you have fixed, try your gpupdate again, and your policy will apply, unless something else is wrong!
Part III, Copying Files, is here.
Categories:
Group Policy
Windows OS-Level Issues
In my experience, group policy is the only nearly indispensable tool on a Microsoft domain-controlled LAN which breaks very often and admits of almost zero solid documentation towards fix. Someday this may be thorough, Lord willing; for now, we have:
Part I, General
Part II, Destrangulation
Part III, Copying Files
Categories:
Group Policy
Windows OS-Level Issues

There are multiple ways to set printers up by group policy in Windows. There is a printer administration role which can make things easier or harder, depending on how well everything is working. The simplest way, is to open the Group Policy Management Console from a domain controller, open up an appropriate policy, and open it to here:
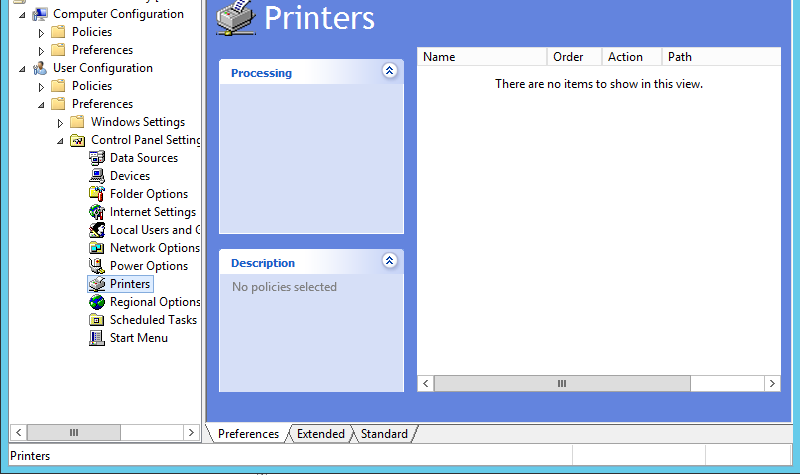
then right-click in the white box, you’ll get a menu, choose “New”, choose “Shared Printer”, Action should be “Update” or “Replace” if “Update” doesn’t work, and you’ll choose the printer by “Share Path”. You can leave everything else alone unless you need something special. Sometimes it works better to do a Delete and then Create for each printer. The vagueness here is due to unknown but widely experienced vagaries in behavior of Group Policy which are addressed in no known documentation.
Please do note that we set these up under “User Configuration” not “Computer Configuration”. It is possible to do it under Computer, but removals can be far more difficult if we do, there have been messes seen.
Categories:
Group Policy
Printers & Printing
To create a shortcut on client desktops by group policy, browse here in GPMC:
User Configuration, Preferences, Windows Settings, Shortcuts
Categories:
Group Policy
To control Internet Explorer settings by group policy, do the following in the Group Policy Management Console (GPMC), after beginning the edit of a policy object:
Open User Configuration, Windows Settings; right-click on Internet Explorer Maintenance, and choose Preference Mode, Advanced. Now on the right pane you will see “Corporate Settings” and “Internet Settings”, and IE can be controlled quite nicely from there. This is a very good way to help control disk space usage on a terminal server, for instance.
Categories:
Group Policy

