Do these in order:
SFC /scannow
DISM /Online /Cleanup-Image /CheckHealth
DISM /Online /Cleanup-Image /ScanHealth
DISM /Online /Cleanup-Image /RestoreHealth
These fix a very large number of issues, 8.1/2012R2 and later. If SFC fails, run it again last, DISM sometimes has to repair the SFC component store. And occasionally, after SFC’s component store has been fixed and SFC rerun, the DISMs need to be done again for completion.
Categories:
Windows OS-Level Issues
Cleanup

Sometimes IPv6 networking goes haywire, on a PC, server, or even a whole network. Machines are there, ping may happen or not, but one, some, or all of them just insist on using oddball IPv6 IPs to connect to each other, even though nothing has been changed voluntarily. Given that even after all these years there still are no useful IPv6 blacklists on the Internet, and given the excellent methods in place to use IPv4, we see no need for IPv6 at this time.
But Microsoft does insist on using IPv6 inside its operating systems, so we must keep it running; disabling v6 does harm in a Microsoft environment. The following is Microsoft’s recommendation to instruct Windows to prefer IPv4, which does eliminate the above issue. One adds a DWORD here:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\
named DisabledComponents. Hex value 20, binary 32. Then reboot.
A quick way to do the registry add, in administrative CMD:
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters /v DisabledComponents /t REG_DWORD /d 32
Still you’ll need to reboot to get it to take effect.
The info is from this reference.
Categories:
Windows OS-Level Issues
IPv6
Categories:
Windows OS-Level Issues

It is very possible. Here is a good way.
Windows 2008 Backup Reporting by Email
I Prepare the script.
The purpose of the script is to actually send the email. We don’t use any built-in email capability, because to do so would make configuration much more complicated. The full text of the script is at the end of this document (as section III). You will need to modify the values for EmailSubject and EmailBody to match the site at which the server is located, and put this modified copy in a good safe location on the server.
The script is pre-configured for gmail. For other ISPs you may need to modify the TCP/IP email port number and/or turn SSL off.
This example will use the location “C:\0DCST\bin”, and the script file name “ReportBackupFailureByEmail.vbs”.
II Insert the script into the Task Scheduler.
1. Open up Task Scheduler, and view the Task Scheduler Library.
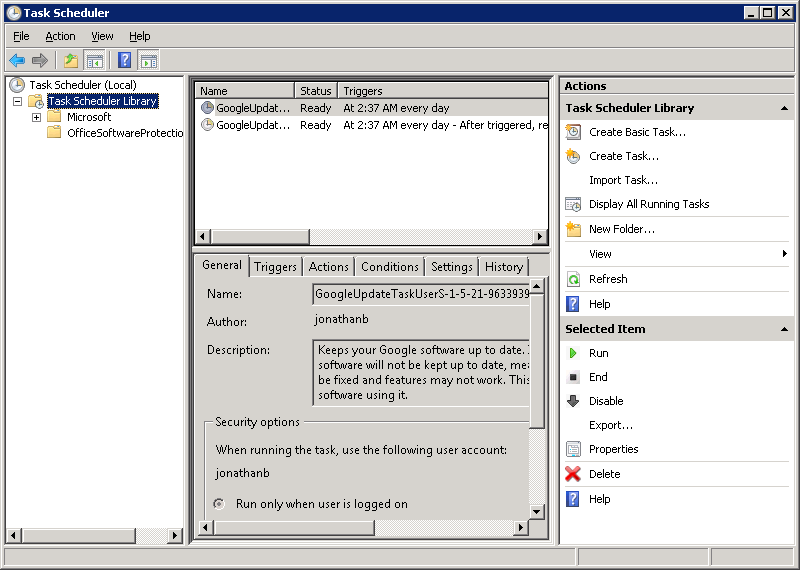
2. Select Create Task… under Actions. This gets you here:
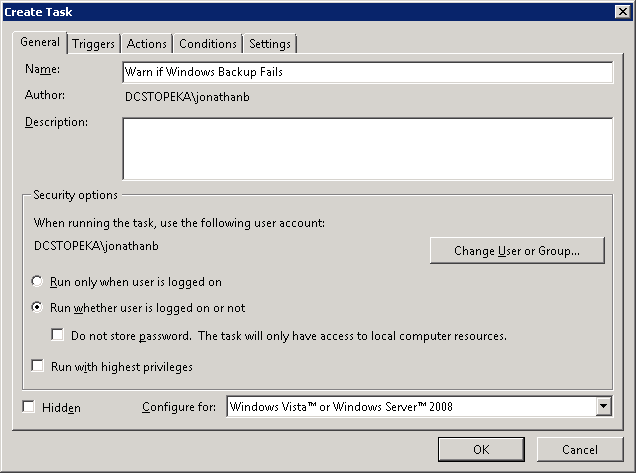
Enter a name and description for your new task. Be sure to select the option to “Run whether user is logged on or not” to ensure the task still runs after you log out.
3. Click on the Triggers tab and click on New. Select “On an Event” from the drop down. Choose “Custom” under Settings.
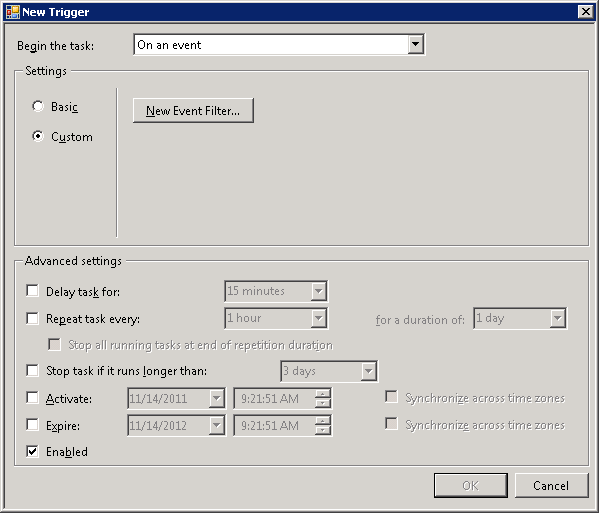
4. Click on “New Event Filter…”. Then, choose as follows:
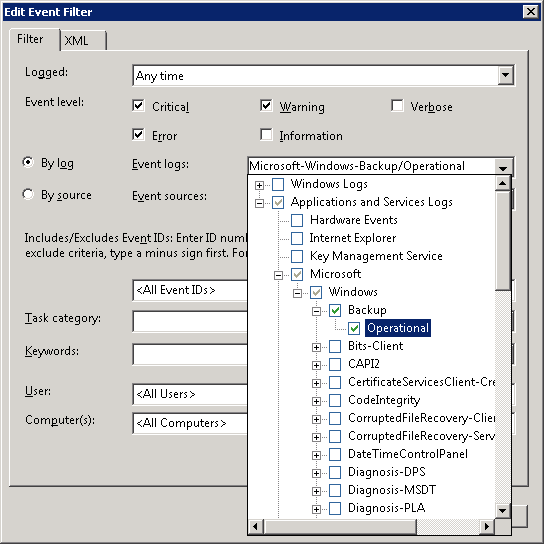
Select all of the event levels except “Information” and Verbose”. Then select “By log”. In the Event Logs dropdown, open Applications and Services Logs, then Microsoft, then Windows, then Backup, and choose Operational.
Once your end result looks like this:
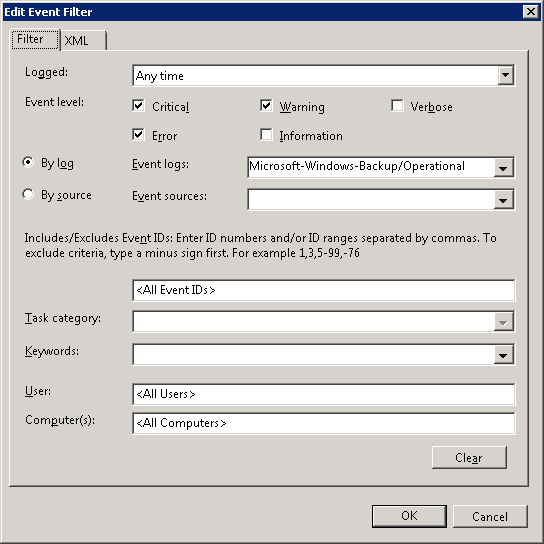
press OK.
5. Head over to the Actions tab and select “New…”. For this example, the following is correct:
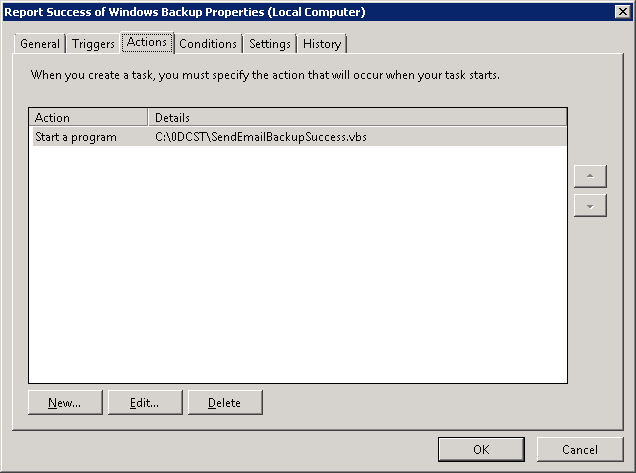
Press OK and OK, put in your authentication, and you’re done!
III The Script:
''''''''''''''''''''''''''''''''''
' Report Backup Failure by Email '
''''''''''''''''''''''''''''''''''
' Script version 1.0
' Needs to be run by Task Manager, triggered by appropriate events
' Modify lines below only to fit site, server, and email configuration
ServerName = "SERVERNAME"
SiteName = "SITENAME"
Const EmailFrom = "emailfrom@gmail.com"
Const EmailFromName = "From Name"
Const EmailTo = "emailto@domain.xyz"
Const SMTPServer = "smtp.gmail.com"
Const SMTPLogon = "emailfrom@gmail.com"
Const SMTPPassword = "gmailpassword"
Const SMTPSSL = True
Const SMTPPort = 465
' Do not modify anything further below
EmailSubject = ServerName & ": Windows 2008 Backup has failed"
EmailBody = "A failure of Windows 2008 Backup has been recorded " & _
"at site " & SiteName & " on server " & ServerName & ", " & _
"on " & Date & ", " & Time & " ."
Const cdoSendUsingPickup = 1 'Send message using local SMTP service pickup directory.
Const cdoSendUsingPort = 2 'Send the message using SMTP over TCP/IP networking.
Const cdoAnonymous = 0 ' No authentication
Const cdoBasic = 1 ' BASIC clear text authentication
Const cdoNTLM = 2 ' NTLM, Microsoft proprietary authentication
' First, create the message
Set objMessage = CreateObject("CDO.Message")
objMessage.Subject = EmailSubject
objMessage.From = """" & EmailFromName & """ <" & EmailFrom & ">"
objMessage.To = EmailTo
objMessage.TextBody = EmailBody
' Second, configure the server
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/sendusing") = cdoSendUsingPort
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpserver") = SMTPServer
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpauthenticate") = cdoBasic
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/sendusername") = SMTPLogon
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/sendpassword") = SMTPPassword
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpserverport") = SMTPPort
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpusessl") = SMTPSSL
objMessage.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpconnectiontimeout") = 60
objMessage.Configuration.Fields.Update
' Now send the message!
objMessage.Send
Categories:
Windows OS-Level Issues
Backup

Mike Hunsinger, who has been addressing Windows Update issues with considerable success over time, recently provided for the following writeup. It is useful when:
- Windows is running slowly or generally unreliably, needs rebooted frequently.
- The Windows Update service spikes CPU usage over 70% when it runs.
- When you check for new updates, it just hangs endlessly on “checking for updates”.
- The last successful update was years ago.
Steps:
- Clean up the system drive.
- Before Server 2012, use Disk Cleanup (cleanmgr.exe). Be sure to check “service pack backup files” and “windows update”, if the version of Windows you are running gives these as options.
- Server 2012 and after, use DISM (dism.exe). Run this in administrative CMD:
dism.exe /online /Cleanup-Image /StartComponentCleanup /ResetBase
If it reports “The operation could not be completed due to pending operations.”, you have just been told that a server reboot is necessary and you’ll need to do this again afterwards. After it succeeds, do this:
dism.exe /online /Cleanup-Image /SPSuperseded
- Run the following as a .bat file to reset Windows Updates caches and working spaces, rereg some dll’s, It works on all versions of windows, may skip some dll’s depending on the OS version:
@ECHO OFF
echo Simple Script to Reset / Clear Windows Update
echo.
PAUSE
echo.
attrib -h -r -s %windir%\system32\catroot2
attrib -h -r -s %windir%\system32\catroot2\*.*
net stop wuauserv
net stop CryptSvc
net stop BITS
ren %windir%\system32\catroot2 catroot2.old
ren %windir%\SoftwareDistribution sold.old
ren "%ALLUSERSPROFILE%\application data\Microsoft\Network\downloader" downloader.old
regsvr32 /s wuaueng.dll
regsvr32 /s wuaueng1.dll
regsvr32 /s atl.dll
regsvr32 /s wups.dll
regsvr32 /s wups2.dll
regsvr32 /s wuweb.dll
regsvr32 /s wucltui.dll
net Start BITS
net start CryptSvc
net start wuauserv
echo.
echo Task completed successfully...
echo.
PAUSE
- Install .net 4.5.1 from here: https://www.microsoft.com/en-us/download/details.aspx?id=40779
- If it says that an =/> version is already installed, run the .net repair tool from here: https://support.microsoft.com/en-us/kb/2698555
- Download the latest version of Windows Update from here: https://support.microsoft.com/en-us/kb/949104
- Next update IE or Edge to the latest version using a redist, here’s the one for EI11, https://support.microsoft.com/en-us/help/18520/download-internet-explorer-11-offline-installer
- Open IE11 or Edge, add update.microsoft.com to trusted sites, popup blocker exceptions, privacy exceptions.
- Finally, try re-running Windows Update. The “Checking for Updates” may run quickly, or it may take 4-6 hours to populate results.
We have had the best results by updating in batches after this, first any critical SP’s or major Platform Updates. Then security, Office and the others as deemed necessary. Once you’ve completed a couple rounds of updates, the difference should start exhibiting itself with regards to the symptoms named.
Categories:
Windows OS-Level Issues
Windows Installer, Updates, Patching
Every scripting language which runs on Windows can call multiple methods of bringing up a popup to users. However, only this CMD method seems to do it for all users, and be callable universally:
msg * /time:9999 /v /w Put your message here!
Categories:
Scripting
Windows OS-Level Issues

Appears to work in Vista, 7, and 8. A whole lot of web references are out there on this. Just one example:
http://helpdeskgeek.com/windows-vista-tips/manage-irq-settings-windows-vista-7/
One studies a list of IRQs and related hardware, and then choose the hardware to maximize priority upon using registry adds. Use msinfo32 (Hardware Resources, IRQs).
We then add registry entries here:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\PriorityControl
It is reported best to include IRQ zero (0) and eight (8) to start with, this is system timer and real time clock. To do these two, add the following-named items as DWORD in the above area, value 1 for the first, value 2 for the second:
IRQ0Priority
IRQ8Priority
When originally looking at this, I was solving a tendency for my softphone to cut out during any load situation or drive access, and so I checked my PC using Device Manager and msinfo32 as above, and also added subseqeuent priorities:
IRQ7Priority
IRQ20Priority
IRQ21Priority
IRQ4294967288Priority
because on this box, 7, 20, and 21 were USB, and 4294967288 was the active NIC. After you have made the changes, reboot.
The above also produced much better response to VNC and RDP redirection via Labtech.
At least one resource states that one must not set the same priority to multiple IRQs. Duplication may be the source of some reports saying it is placebo effect. Here is a very interesting post with some seriously good-quality testing and results:
https://www.tenforums.com/performance-maintenance/140553-regedit-priority-control-irq.html#6
Categories:
Windows OS-Level Issues
Performance
Several fixes, some of them most interesting:
https://www.guidingtech.com/fixes-for-chrome-not-opening-on-windows/
Number 4 on that page, is most surprising, and often functional with new build upgrades.
Recommended by the amazing Yvonne Wynkoop.
Categories:
Windows OS-Level Issues
Google Tools

There is some definite undocumented mystery concerning Volume Shadow Services in Windows. In general we are told to use VSSADMIN to do maintenance, and it does a lot, and helps a lot. But recently there was a Server 2012 R2 machine using 280G of space for System Volume Information on C:, and after CHKDSK and various DISMs it still was using 280G. So I tried removing all orphan shadows with VSSADMIN, and it found one and removed it; almost zero change comparatively. And then I searched a little deeper.
DISKSHADOW is built into Windows 2012 R2 and later, and earlier too I think, not sure how early. It may be a successor to VSHADOW which was an SDK add-on to 2003. Regardless, DISKSHADOW is a command-line environment of its own sort of like NSLOOKUP and DISKPART (!), not a simple command, can run a script of its own commands, and one of its commands is:
DELETE SHADOWS ALL
Now VSSADMIN DELETE SHADOWS /ALL deletes all orphan shadows, all VSS shadow copy sets which Windows knows are good to delete. The above within DISKSHADOW is a different animal altogether: it deletes them all. And does not appear to report anything to event logs (!). And definitely frees up a whole lot of space. And also, definitely not least, is flagged as infection activity by certain high-test super-anti-malware tools, when run! That was amazing, a Windows built-in being run with one of its own recommended commands, flagged. But I’ll think that that means this is to be used only when very needed. There may be gotchas I don’t know about yet.
As I write, the System Volume Information on this C: drive has been shrunken 290 (two hundred ninety) gigabytes, and everything is still running fine. There were originally 522 (five hundred twenty-two) shadow copies hanging out there of many different sizes, and DISKSHADOW was able to delete them all, all server services appear AOK.
Categories:
VSS
Windows OS-Level Issues

Well, it rocked my little world. This came from the excellent Terry Powell. He had a Server 2016 machine where Explorer would crash and restart every time Devices and Printers was opened. A very large number of common fixes was tried, including four different DISM methods with SFC and others, no change, DISM said the image was fixable but nothing would fix, and the only thing clearly missing according to DISM and SFC logs was a .lnk file. Terry found a reference stating that if one clears everything here except “(Default)”:
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Devices
and then restarts the printer spooler, all begins working well. And indeed, it appears that this is space in which bad gunk can build up! He found about 100 there, removed them, and lo and behold, all is well. Powershell code to do this:
function Remove-AllItemProperties
{
[CmdletBinding()]
param([string]$Path)
Remove-ItemProperty -Name * @PSBoundParameters
}
Remove-AllItemProperties "HKCU:\SOFTWARE\microsoft\windows nt\currentversion\devices"
Stop-Service Spooler
Start-Service Spooler
Categories:
Printers & Printing
Windows OS-Level Issues





