Since Windows 7, I have been adding the Everyone group to Windows-hosted printers, and checking every permissions box, as a method to drastically increase reliability and controllability, using other groups only if restrictions were necessary. The inestimable Dave Gottschamer just reported a scenario in which Everyone was there, but didn’t work; he tried Authenticated Users and it worked. This is quite the sea change. Not exactly unexpected, as Microsoft has been slowly denaturing Everyone for quite some time, but now we have a definite diagnostic-and-fix change for printers, including desktop USB printers, which will help!
Category: Printers & Printing
Security in Windows Printing: A Sea Change
article #1600, updated 285 days ago
When bad printers show up, print-over-RDP doesn't work, and GPO is clear
article #1459, updated 1243 days ago
If group policy cache is clear, group policy bugs are ironed out, and you still see bad/nonfunctional printers forcibly recreated and/or print-over-RDP doesn’t work, try this (you’ll need psexec) in administrative CMD:
psexec.exe -s reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Print\Providers\Client Side Rendering Print Provider" /f
psexec.exe -s reg delete "HKLM\SYSTEM\CurrentControlSet\Enum\SWD\PRINTENUM" /f
psexec.exe -s reg add "HKLM\SYSTEM\CurrentControlSet\Enum\SWD\PRINTENUM"
psexec.exe -s reg delete "HKLM\SYSTEM\CurrentControlSet\Control\DeviceClasses\{0ecef634-6ef0-472a-8085-5ad023ecbccd}" /f
psexec.exe -s reg add "HKLM\SYSTEM\CurrentControlSet\Control\DeviceClasses\{0ecef634-6ef0-472a-8085-5ad023ecbccd}"
Any SMB-mapped printers will be deleted or grayed, IP direct printers will remain.
32-bit printer driver in 64-bit server! And the other way around!!!
article #129, updated 1371 days ago
OK, so we have that problem increasingly common, a 64-bit server, trying to serve a printer to 32-bit client machines, or vice versa. It took me a while, but here are two different methods I have needed, depending on situation.
First, see if current drivers are downloadable for this printer in the server’s mode (bit-width). If they are, we are able to use method #1, which is probably preferable, although method #2 may still work too. Here’s method #1:
- Download them in both 32-bit and 64-bit versions, install the printer to the server in its preferred (32- or 64-bit) mode, and test. Unpack the other driver in a good location, you will need it soon.
- Get the printer properties up, go to the Sharing section, set up sharing. Don’t publish to the Active Directory yet or you might drive somebody crazy. Click on Additional Drivers.
- You’ll notice “x86” or “x64” is unchecked, because you haven’t installed the other driver yet. Check it, and then hit OK. The system will now demand to be directed to where you have unpacked the other driver. Do so. It might work just at this point! But…
- …it may ask you for one of two additional things. It may ask for 32-bit install media; or, it may ask for particular files, e.g., ntprint.inf, or ntprint.in_, in 32-bit mode. It’s important to realize that the 32-bit requirement is for equivalent OS: a 2008R2 install requires files from 32-bit Windows 7, 64-bit Server 2008 requires files from 32-bit Vista, and 64-bit Server 2003 requires files from 32-bit XP. If you can supply these files, do it, and you’ll be done shortly; it has to be done just once per server, not per printer. If you cannot do this, you’ll need to use method #2.
If you cannot use method #1, or if there are no downloadable drivers for your printer, we go to method #2:
- If there are no downloadable drivers from the printer manufacturer, install the printer to the server using Windows built-in drivers. Under Windows 7 / 2008R2, there is a “Windows Update” clickable in the driver list, by which you can retrieve a much larger set of drivers than is included by default; this is highly recommended. The included Microsoft generics may help, there is a PCL6 and a PS.
- If there are downloadable drivers from the printer manufacturer, for the server OS, use them.
- Install the printer to the client. If you’re using Windows Update or built-in drivers on the server, use them on the client too. Otherwise, make sure that the client drivers are the same type as the server’s, i.e., PCL6 and PCL6, PCL5e and PCL5e, PS3 and PS3.
- On the client, log in as network administrator. Open up the properties of the printer. Click on Advanced. Click on New Driver. Notice the name of the wizard: you’re actually installing a driver onto the server, not onto the client!
- Choose the driver you want to install onto the server. Click Next et cetera. Watch the client driver install onto the server, over the network!
- Check it out the drivers on the server, Shared tab, Additional Drivers button. You’ll see one you need listed. You are done!
- If the New Driver method does not work, try doing approximately the same from within the Additional Drivers button; it works also, to add drivers to server from workstation, as long as you’re logged in as network admin.
A Windows Print Spooler World-Shaker
article #1414, updated 1551 days ago
Well, it rocked my little world. This came from the excellent Terry Powell. He had a Server 2016 machine where Explorer would crash and restart every time Devices and Printers was opened. A very large number of common fixes was tried, including four different DISM methods with SFC and others, no change, DISM said the image was fixable but nothing would fix, and the only thing clearly missing according to DISM and SFC logs was a .lnk file. Terry found a reference stating that if one clears everything here except “(Default)”:
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Devices
and then restarts the printer spooler, all begins working well. And indeed, it appears that this is space in which bad gunk can build up! He found about 100 there, removed them, and lo and behold, all is well. Powershell code to do this:
function Remove-AllItemProperties
{
[CmdletBinding()]
param([string]$Path)
Remove-ItemProperty -Name * @PSBoundParameters
}
Remove-AllItemProperties "HKCU:\SOFTWARE\microsoft\windows nt\currentversion\devices"
Stop-Service Spooler
Start-Service Spooler
Microsoft Printing Troubleshooter
article #1345, updated 2006 days ago
Does not seem to have a web page of its own, it is linked from others:
Windows printer setup automation by script: Installation
article #1229, updated 2470 days ago
Recently there was a case where a Windows Server 2016 print server was set up, and very odd things happened vis a vis one particular large MFP: When any non-admin user changed printer settings on her/his PC only, those settings were replicated to all users on all PCs who had that printer. Microsoft printer deployment was doing it somehow; testing was done both using Print Management and the other GPO print setup method, same result. When manual mappings were used to replace the deployments via Windows Explorer, the symptom went away.
Thus the CMD script below. It can be run as administrator from a PC or remotely via psexec, or a variety of other ways. It installs the driver into the PC, and via scheduled task, any new user that logs into the PC, will have his/her own new mapping to the printer.
@ECHO OFF ECHO. ECHO This script will (a) install the driver for a server-shared ECHO printer into a PC by UNC, and (b) set up a Scheduled Task ECHO to map that printer to any user at logon if they have ECHO permissions for that printer. ECHO. ECHO It has to be run as administrator, and it requires ECHO two command line arguments: ECHO. ECHO first, a unique, optionally quoted, short name for the printer, ECHO used in the task name only; ECHO and second, the quoted UNC path of the printer. ECHO. ECHO If the unique name already exists in the system, ECHO it will be overwritten. The short name can have no slashes. ECHO. :: 1. Get printer printer UNC path via command line. :: :: 2. Install printer driver into PC. This is done by a RUNDLL install of the printer to the administrator user, :: and is one of two reasons this script has to be run as administrator. :: Example: rundll32 printui.dll,PrintUIEntry /q /in /n "\\machine\printer" :: :: 3. Set up scheduled task, to be run at user logon and using user creds, to install the printer to the user profile. :: First we do have to dequote the variables. Set UniqueName=%~1 Set UNCpath=%~2 :: Step 1. ECHO Printer to be set up: %UNCpath% ECHO Using short name: %UniqueName% ECHO. :: Step 2. :: Install the printer into PC as administrator. ECHO Installing printer as administrator, to get driver in... rundll32 printui.dll,PrintUIEntry /q /in /n "%UNCpath%" ECHO. :: Step 3. :: Set up the at-login scheduled task... ECHO Set up the at-login scheduled task... Set RunString=%windir%\System32\rundll32.exe printui.dll,PrintUIEntry /q /in /n echo Task will run: %RunString% %UNCpath% schtasks /Create /F /SC ONLOGON /TN "%1" /TR "%RunString% \"%UNCpath%\"" ECHO. ECHO Script completed.
Windows network printer changes in CMD
article #1026, updated 2470 days ago
Very easy:
Quietly install a network printer – per user
rundll32 printui.dll,PrintUIEntry /q /in /n "\\machine\printer"
Quietly delete a named network printer – per user
rundll32 printui.dll,PrintUIEntry /q /dn /n "\\machine\printer"
Set default printer
rundll32 printui.dll,PrintUIEntry /y /n "\\machine\printer"
Quietly install a network printer – per machine
rundll32 printui.dll,PrintUIEntry /q /ga /n "\\machine\printer"
Quietly delete a network printer – per machine
rundll32 printui.dll,PrintUIEntry /q /gd /n "\\machine\printer"
Quietly delete a specific printer driver
rundll32 printui.dll,PrintUIEntry /q /dd /m "PrinterDriver"
Get rid of the new Windows-controlled default printer setup
article #1225, updated 2476 days ago
Windows 10 has some sort of automatic thing built in which is pretended to read our minds and decide for us which of our printers should be the default at any time. Needless to say this makes no sense at all, and causes lots of user frustration. To turn this off with Group Policy, browse to:
User Configuration -> Administrative Templates -> Control Panel -> Printers
and set “Turn off Windows default printer management” to Enabled.
Windows printer management using built-in VBS scripts at the command line
article #837, updated 2675 days ago
From Windows 7 on, Microsoft has thoughtfully provided us with VBS scripts for command-line printer management, here:
C:\Windows\System32\Printing_Admin_Scripts
In this dot on the globe, we go to the following system folder to see them all, there are several:
C:\Windows\System32\Printing_Admin_Scripts\en-US
To delete printer named ASDF:
cscript C:\Windows\System32\Printing_Admin_Scripts\en-US\prnmngr.vbs -d -p "ASDF"
Setting Up Printers by Windows Group Policy the Simplest Way
article #1113, updated 2778 days ago
There are multiple ways to set printers up by group policy in Windows. There is a printer administration role which can make things easier or harder, depending on how well everything is working. The simplest way, is to open the Group Policy Management Console from a domain controller, open up an appropriate policy, and open it to here:
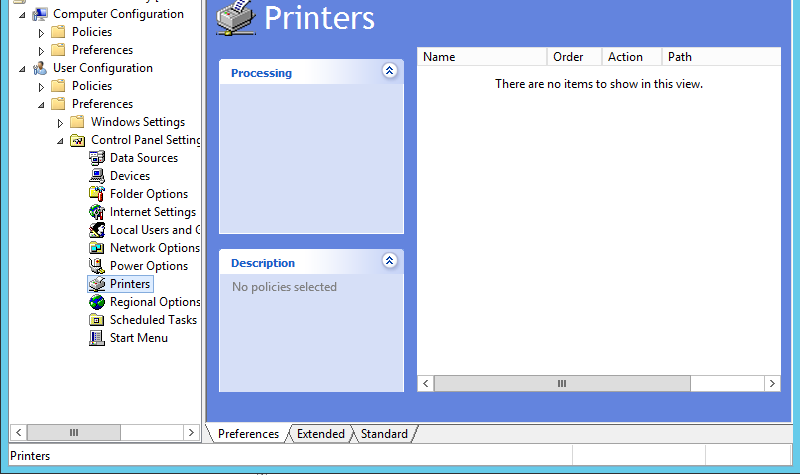
then right-click in the white box, you’ll get a menu, choose “New”, choose “Shared Printer”, Action should be “Update” or “Replace” if “Update” doesn’t work, and you’ll choose the printer by “Share Path”. You can leave everything else alone unless you need something special. Sometimes it works better to do a Delete and then Create for each printer. The vagueness here is due to unknown but widely experienced vagaries in behavior of Group Policy which are addressed in no known documentation.
Please do note that we set these up under “User Configuration” not “Computer Configuration”. It is possible to do it under Computer, but removals can be far more difficult if we do, there have been messes seen.